Windows Mini Class and Class Driver internal research notes
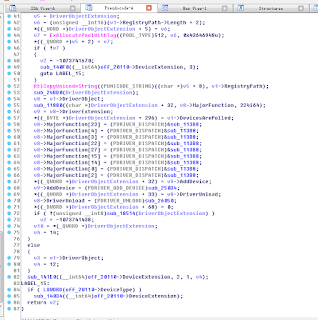
Background ------------------------------------- This is a first windows driver research notes in my blogger. And I will try to keep it simple and clear in this article, for who wants to understand the internal behavior of Class And Mini-Class Driver. ------------------------------------- Audience ------------------------------------- For who wants to understand Mini-Class and Class Driver internal. And understanding more about Hid Device stack. ------------------------------------- Introduction ------------------------------------- First, We are going to take a example of HidUsb and HidClass, the former is a Mini-Class Driver of a HidClass. We can simply think the relationships between them, is a child and parent relationship, Hidusb is one of the child of HidClass. HidClass can be thought as a helper module( like Dll do) in kernel mode, for helping all Driver who wants to join a hid family. ------------------------------------- Research ----...

